
Telefonica, NHS Hit by Massive Ransomware Attacks
Anti-Malware
,
Cybersecurity
,
Risk Management
Leaked ‘Shadow Brokers’ Exploit Apparently First Used Against Telefonica
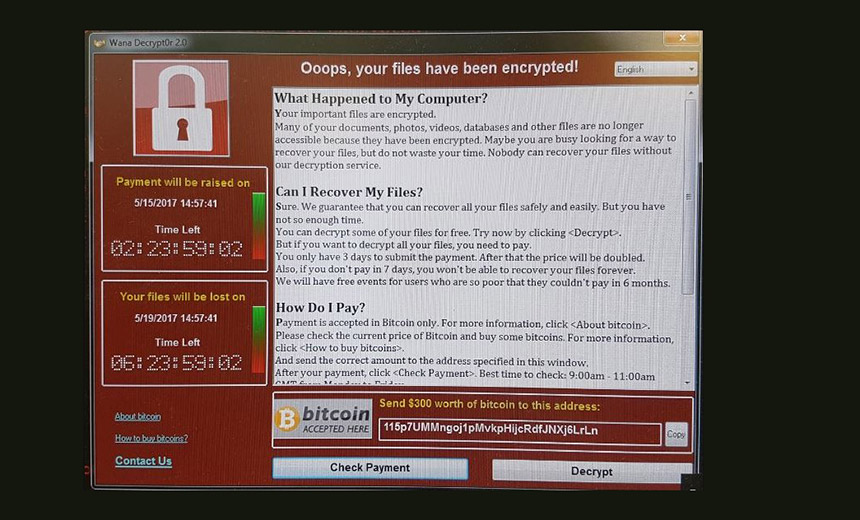
Spanish telecommunications giant Telefonica has reportedly instructed all employees to power down their systems in the wake of a massive ransomware attack. In addition, multiple National Health Service trusts in England say they’ve been hit with ransomware.
See Also: Balancing Fraud Detection & the Consumer Banking Experience
It’s not clear if the incidents are related, although both have reportedly led to widespread ransomware infections and caused multiple organizations to deactivate all endpoints as a precautionary measure. Both attacks appears to have infected endpoints with the WannaCry crypto-locking ransomware, which is also known as WCry and WanaCrypt0r.
Two security professionals with access to details surrounding the Telefonica incident say that attackers appear to have breached Telefonica’s network – after which they deployed the WannaCry ransomware – by using the DoublePulsar “Shadow Brokers” exploit leaked in April by the Shadow Brokers (see DoublePulsar Pwnage: Attackers Tap Equation Group Exploit).
The Shadow Brokers is the shadowy group believed to tie to the Russia government, while the Equation Group appears to be the National Security Agency’s in-house hacking team, known as Tailored Access Operations.
Telefonica couldn’t be immediately reached for comment.
DoublePulsar is an exploit that was patched in April by Microsoft in the form of MS17-010. That security update patches a server message block, or SMB, server vulnerability present in every Windows operating system from XP to Server 2008 R2, and which appears to have been used by the Equation Group to gain access to targeted networks, at which point additional attack tools could be deployed.
NHS: Major Emergencies Declared
At least 16 NHS trusts in England have been hit by ransomware infections, Sky News reprts, leading the organizations in some cases to declare major emergencies and redirect patients – including to accident and emergency departments – to other locations.
Colchester General Hospital, for example, has shut down all computer systems as a precautionary measure, Sky News reports, and issued a statement saying it was “postponing all non-urgent activity for today and we are asking people not to come to A&E.”
Britain’s national fraud and cyber reporting center, ActionFraud, confirms that multiple NHS trusts and hospitals – in London, Nottingham, Blackburn, Cumbria and Hertfordshire – have been hit in the attacks. Infected endpoints are demanding $300 in bitcoins, it says, adding that intelligence agency GCHQ’s National Cyber Security Center is aware of the incident and working with the NHS and the National Crime Agency’s National Cyber Crime Unit.
NHS computers have been locked by Wanna Decryptor #ransomware. To protect yourself in the future, follow our advice https://t.co/DVtbNKSk7X
— Action Fraud (@actionfrauduk) May 12, 2017
“The investigation is at an early stage but we believe the malware variant is Wanna decryptor,” an NHS Digital spokeswoman says. “NHS Digital is working closely with the NCSC, the Department of Health and NHS England to support affected organizations and to recommend appropriate mitigations. This attack was not specifically targeted at the NHS and is affecting organizations from across a range of sectors.”
The ActionFraud alert also included a copy of this tweet by journalist Lawrence Dunhill:
Here’s the malware attack which appears to have hit NHS hospitals right across England today pic.twitter.com/zIAJ6wbAG5
— Lawrence Dunhill (@LawrenceDunhill) May 12, 2017
Watch for updates to this developing story.


